A Brief Overview of Sigma
Why do I like Sigma?
If you've read any of my posts, you've noticed that I'm a big proponent of the Sigma project. Whenever I set out to write detection rules, I do so in this format.
Note: I'm also in the process of contributing some MacOS Sigma rules for overlooked LOOBins and plan to contribute more in general.
This particular post is for readers who aren't yet familiar with Sigma and would like to learn more.
What is it?
Sigma was first released in 2017 by Florian Roth and Thomas Patzke. At the lowest level, it is an open-source and shareable detection rule format.
What problem does it solve?
Vendor Lock-in
One big benefit that Sigma provides is avoiding vendor lock-in. Instead of writing detection rules or queries in a vendor specific format (whether SIEM, EDR, XDR, etc. ), one can write them in the Sigma format and then use the conversion tool to get them compatible with the vendor Platform of choice.
This prevents the scenario where an organization has a large amount of custom rules/queries written for vendor Platform X and would like to move to vendor Platform Y, but the overhead of manually converting the rules/queries and learning the new formatting makes it a tenuous decision.
Shareable
Another advantage of using the Sigma format is the ability to share detection rules in an agnostic way. Any researcher/defender/intel analyst can craft and share a rule that can be converted to all of the major vendor Platforms with very minimal overhead.
This enables rapid detection opportunities in the face of an emerging threat. This also means that a community approach to rule sharing is in play. There is an excellent existing repository of over 3000 community created rules that anyone can use free of charge.
What does the process look like?
Thankfully, the format uses YAML and is fairly easy to understand/use.
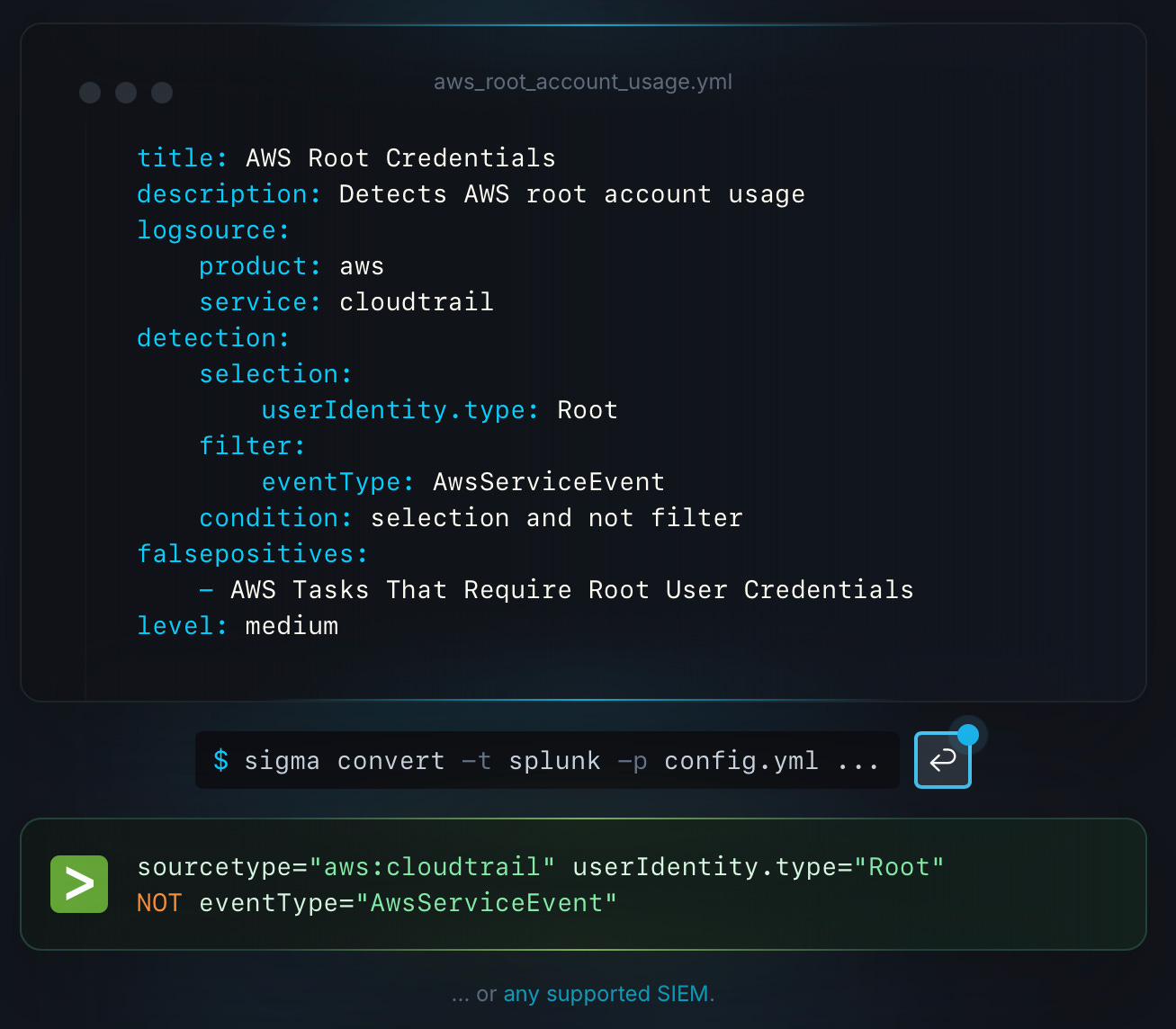
The process at a high-level consists of: new rule in .yml>run conversion>add to vendor Platform of choice -
Here is a closer look at the process with an example -
What does a typical rule look like?
All the details of what’s needed for a rule can be found in this excellent guide.
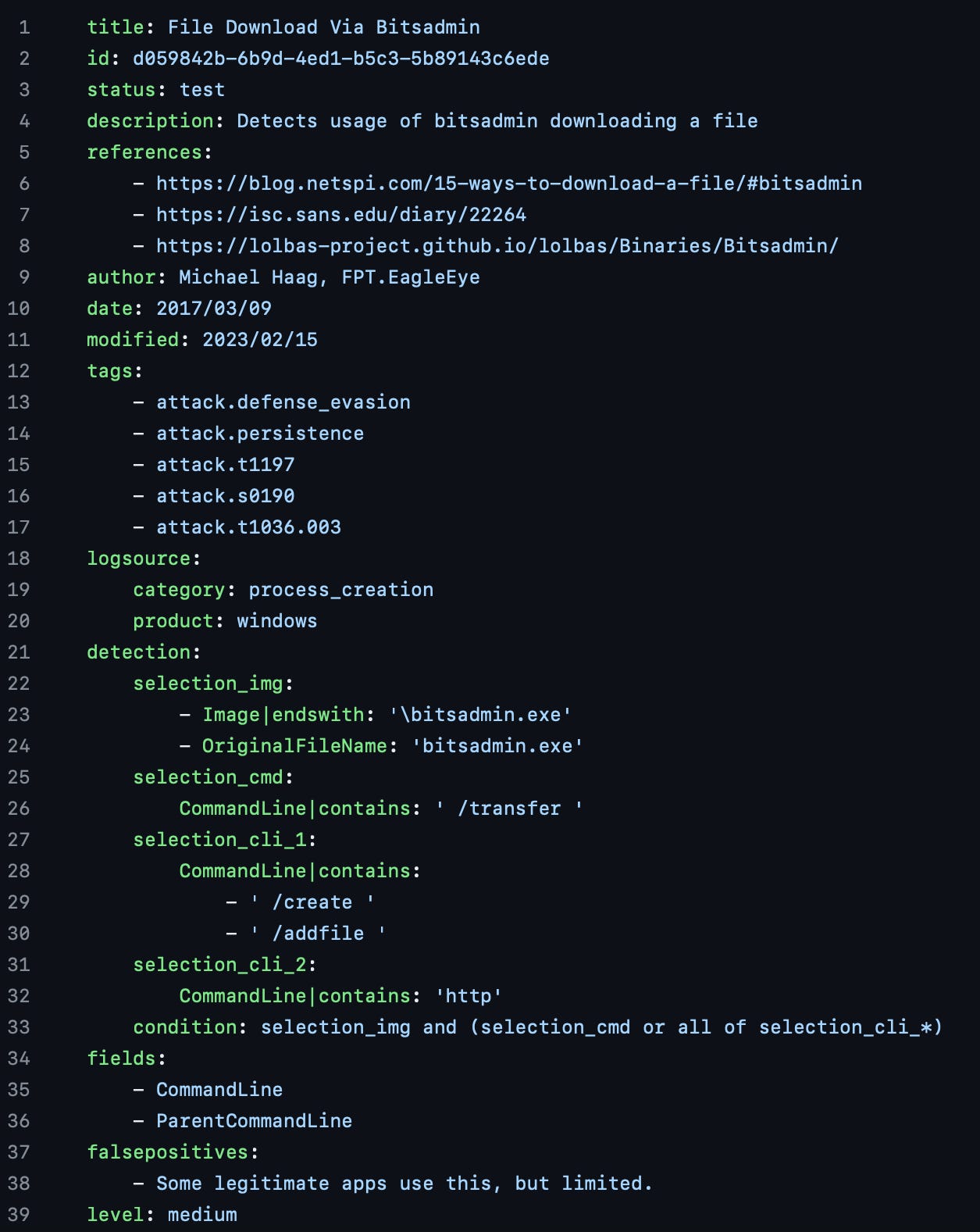
Here is an example of a basic rule under the windows>process_creation directory: proc_creation_win_bitsadmin_download.yml
As you can see, the format is very readable and includes important metadata fields like ATT&CK “tags” and “references”.
Conclusion
If you’ve read this, hopefully it was helpful and you now have a baseline understanding of Sigma. Feel free to contribute to the repository and support open-source projects like this for the Cybersecurity community!