Living-off-the-Land: Exploring macOS LOOBins and Crafting Detection Rules - nscurl
Exploring lesser known Living-off-the-Orchard Binaries and creating Sigma rules for detection
LOL Overview
In Cybersecurity, there is a concept known as Living-off-the-Land (LOL or LOTL) , wherein adversaries stick to using things like binaries, scripts, and drivers built into the Operating System to carry out their attacks - rather than using specialized hacking tools.
This technique can be extremely effective because the malicious actions are able to blend in with normal activity and may not appear suspicious at first glance. In fact, many of the LOLBins (LOL Binaries) are used regularly by Administrators, Applications, and Processes and/or are expected, whitelisted, and pre-approved by Security Tools.
Additionally, security departments on the lower end of maturity are often not looking for this activity and may not even realize that legitimate OS binaries can be misused in this manner.
These days, the term Living-off-the-Land is mostly reserved for Windows. Here are two sites with tons of documentation that I highly recommend reading through to become more familiar with this concept on the Windows side : LOLBAS and LOLDrivers
The Windows side has been explored and is well-known, however, this post/series will focus on the often-overlooked macOS side: LOOBins (Living-off-the-Orchard Binaries).
The first entry in this series is ‘/usr/bin/nscurl’.
nscurl
While ‘curl’ is a common binary and frequently used across all platforms (Windows, Linux, macOS), ‘nscurl’ is unique to macOS but can be used in similar ways.
Normal Usage
Developers can use ‘nscurl’ to troubleshoot ATS (App Transport Security) connection issues with their applications. See examples here
Misuse
Note: The downloaded app used in these examples is merely for demonstration purposes - the download could be anything.
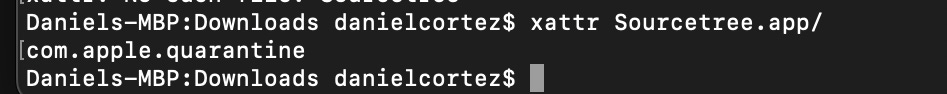
The ‘nscurl’ binary also provides the ability to download files from remote sources onto the target machine. One key aspect, using ‘nscurl’ for downloads prevents the quarantine extended attribute (“com.apple.quarantine”) from being added to the file.
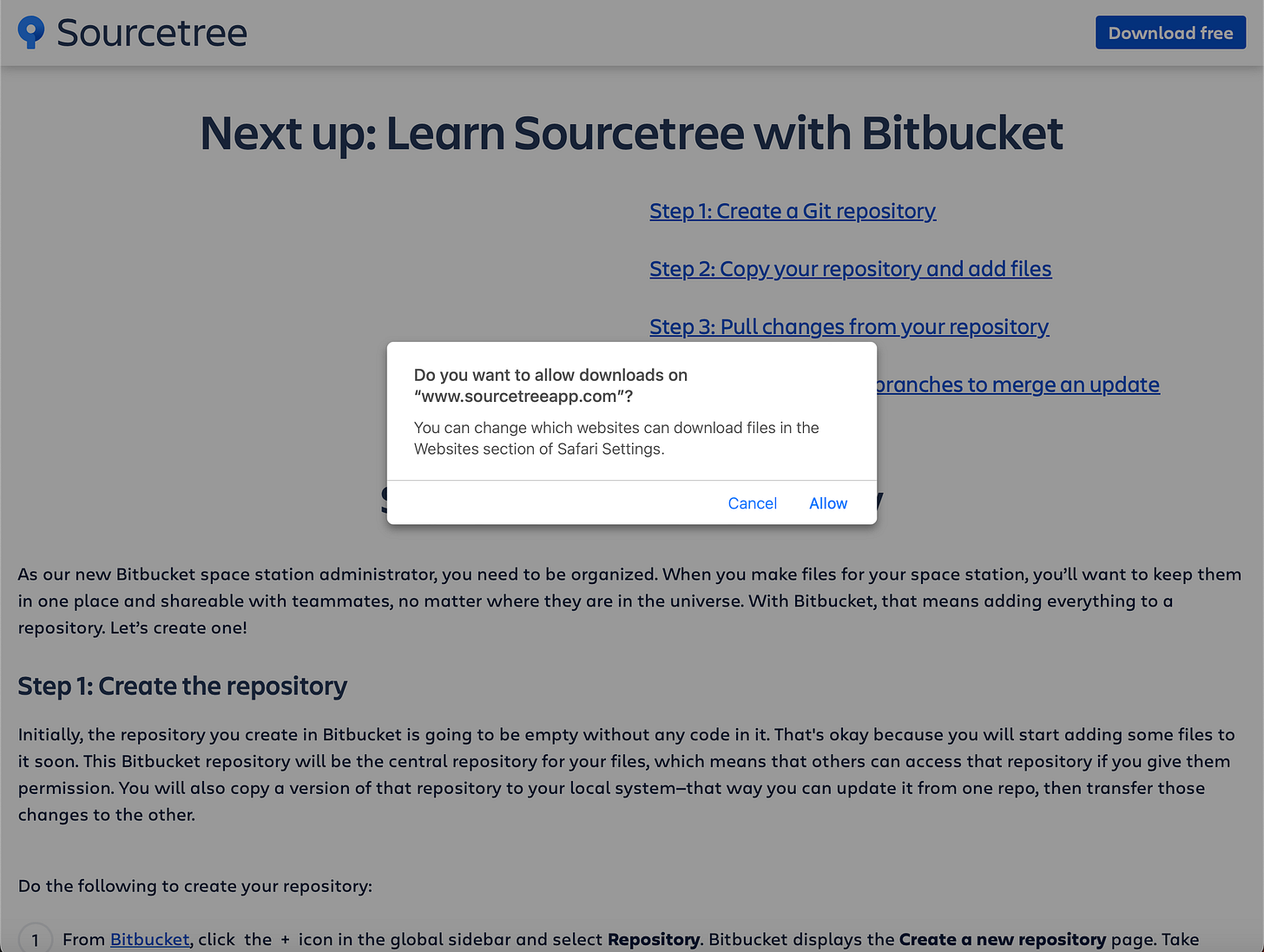
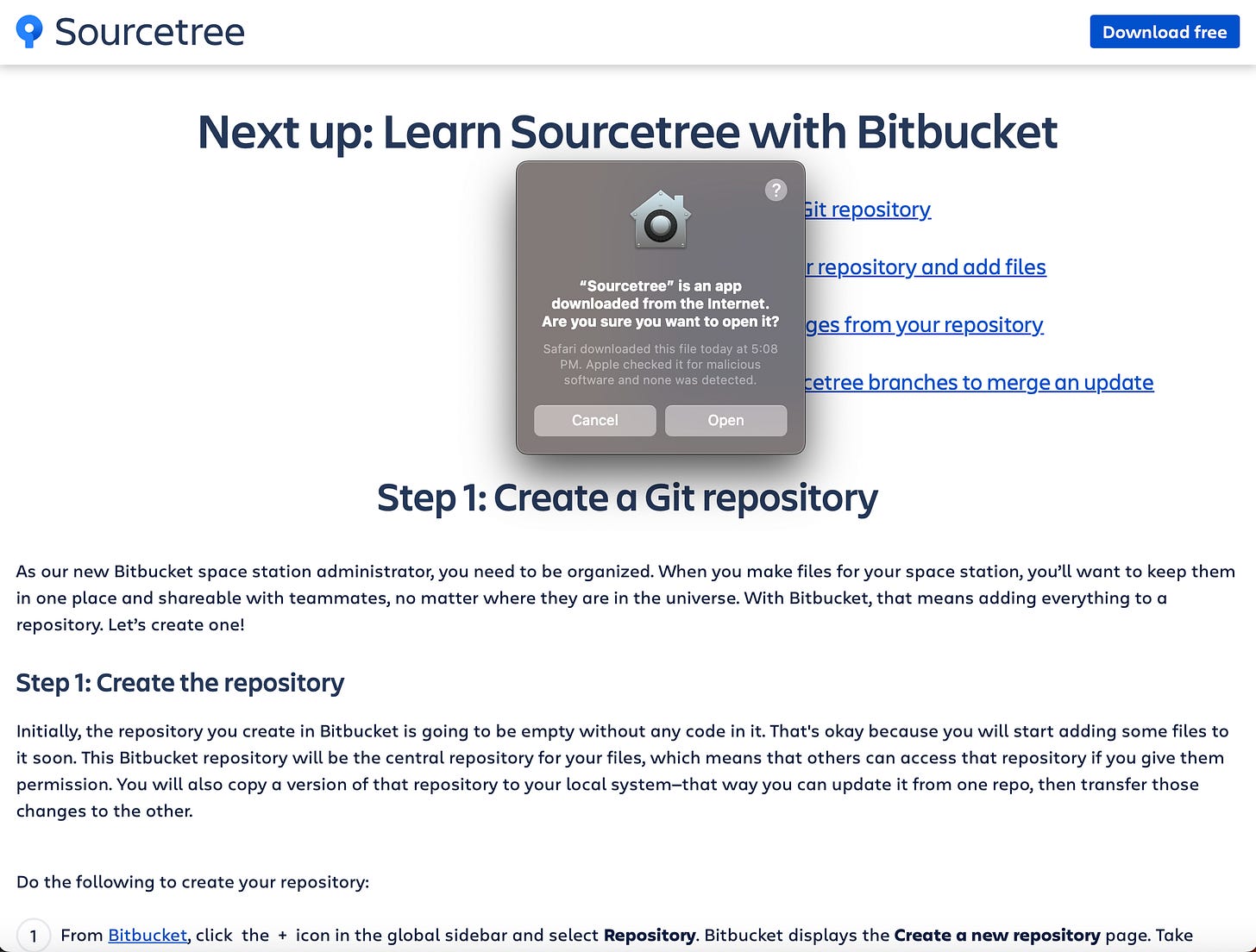
Normally, files downloaded through Safari include this attribute and multiple warnings are given:
“Allow Downloads” Example:
“App Downloaded from the Internet” Example:
Quarantine Extended Attribute Example (Downloaded via Safari):
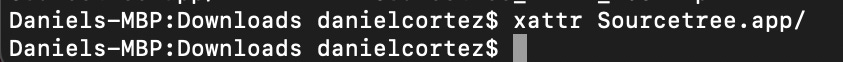
Now, if a file is downloaded via ‘nscurl’, then the quarantine attribute is not present (the ‘xattr’ command on the file doesn’t return anything):
Example Download Commands
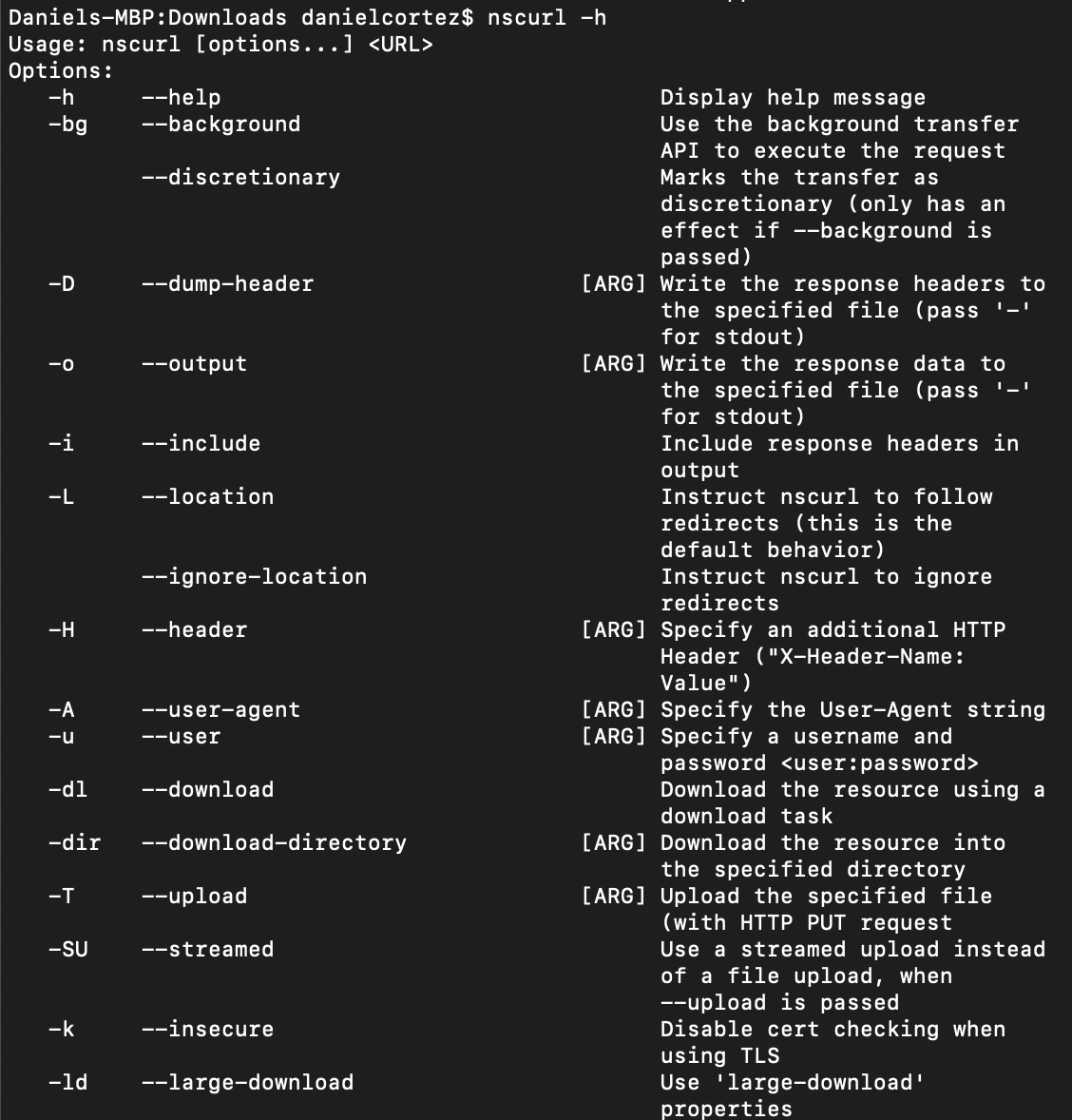
To view available usage options, run:
nscurl -hIt should return something like this (not all options are included in this screenshot):
The options that stuck out to me for downloads were: ‘-o’ for output, ‘-dl’ for download, and ‘-dir’ for download directory.
-o
Command syntax can look something like this:
nscurl <path-to-remote-file> -o <path-to-output-directory/file> Example:
-dl
Command syntax can look something like this (the remote file gets placed in the “Downloads” directory):
nscurl <path-to-remote-file> -dlExample:
-dir
Command syntax can look something like this:
nscurl <path-to-remote-file> -dir <path-to-output-directory> Example:
Detection Opportunities
There were previously no existing Sigma Rules to detect this behavior with the ‘nscurl’ binary. To help out with this, I went ahead and crafted a Sigma Rule to contribute to the Master Repository. Here is the detection rule:
title: File Download Via Nscurl - MacOS
id: 6d8a7cf1-8085-423b-b87d-7e880faabbdf
status: experimental
description: Detects the execution of the nscurl utility in order to download files.
references:
- https://www.loobins.io/binaries/nscurl/
- https://www.agnosticdev.com/content/how-diagnose-app-transport-security-issues-using-nscurl-and-openssl
author: Daniel Cortez
date: 2024-06-04
tags:
- attack.defense-evasion
- attack.command-and-control
- attack.t1105
logsource:
category: process_creation
product: macos
detection:
selection:
Image|endswith: '/nscurl'
CommandLine|contains:
- '--download '
- '--download-directory '
- '--output '
- '-dir '
- '-dl '
- '-ld'
- '-o '
condition: selection
falsepositives:
- Legitimate usage of nscurl by administrators and users.
level: mediumThis rule is looking for:
Process Creation events
on macOS
Using the ‘nscurl’ binary
With either ‘-o’, ‘-dl’, ‘-dir’, or ‘-ld’ options in the command line
Since this usage is not normal, false positives are expected to be unlikely and any alerts should be investigated.