Welcome to the first entry in my series on Ransomware Groups! We’ll start with some quick background information on the threat group and include links to IOC’s/more detailed analysis. Then we’ll dive into some tactics, techniques, and procedures (TTP’s) mapped to the MITRE ATT&CK framework, along with basic detection strategies (example Sigma rules included).
Note: It goes without saying that a holistic security program is needed and defense in depth strategies should be followed. I’ll be focusing more on detection strategies since these often get overlooked (plus they’re more interesting to me).
Introduction
At this point in 2024, everyone that uses a computer should be familiar with Ransomware and the potential impacts it can have on an organization. Ransomware is a growing threat to all industries and organizations of all sizes (small to medium business included). As such, it’s critical for defenders to be aware of the different groups/variants active in the wild and to be equipped with the necessary information to protect their organizations against these threats.
Image generated by DALL-E
What is LockBit?
LockBit is a Ransomware variant that operates in a Ransomware-as-a-Service (RaaS) model. Essentially, the LockBit group develops and maintains these malicious tools and sells access to individuals or other groups (affiliates) that want to use them to conduct their own attacks. In return, the development group can either receive subscription fees, upfront payments, or a cut of the paid ransom (among other agreed upon terms). RaaS models have turned into big business and are continuing to expand.
The LockBit group has established itself as the dominant Ransomware variant over the last 2 years (2022-2023). They have been able to grow quickly by employing businesslike processes and making their tools easy to use. They have consistently made headlines with high-profiles victims such as Boeing and the UK’s Royal Mail.
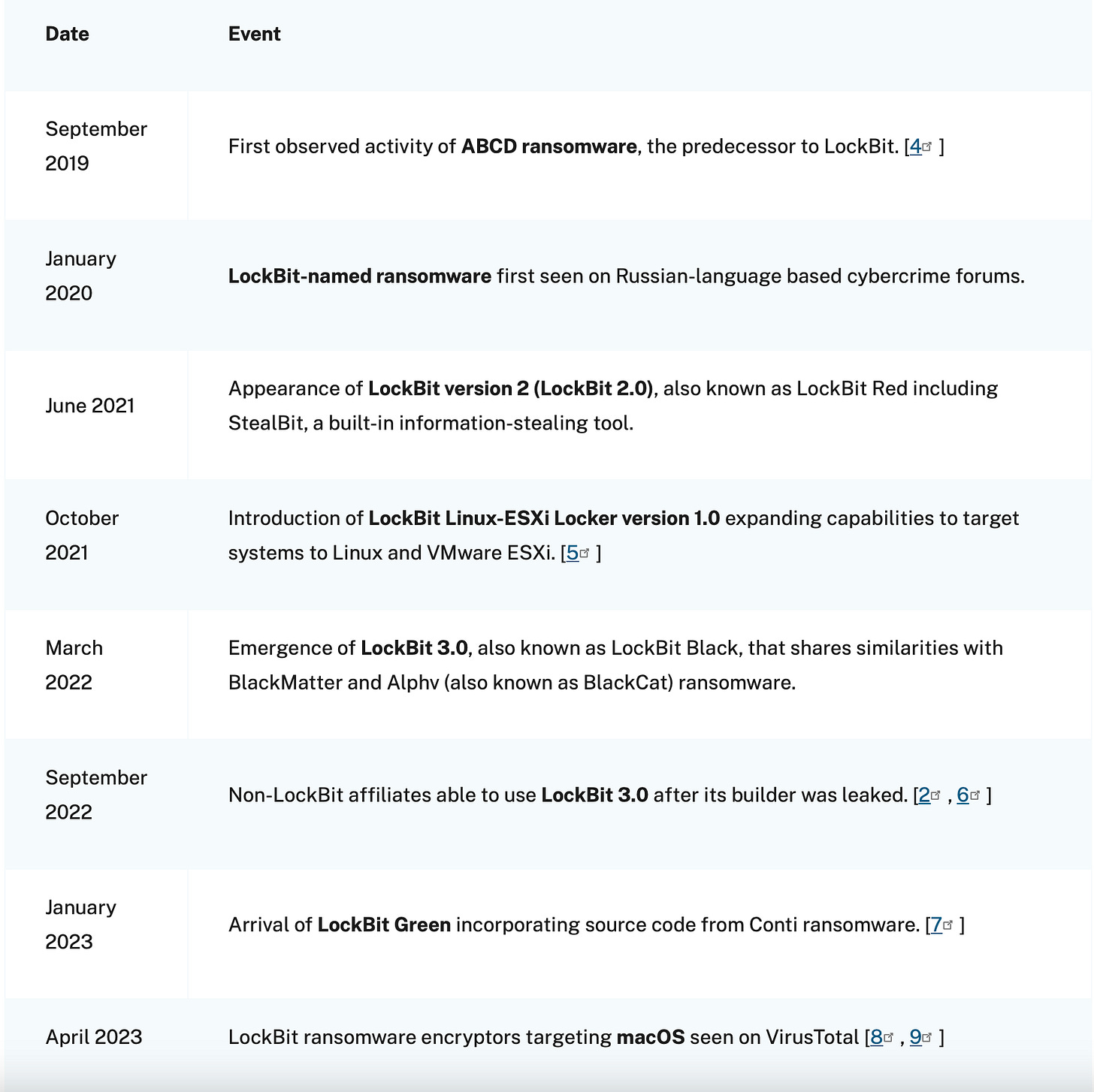
We can see a timeline of their version development here:
LockBit Timeline (From CISA Report)
Ultimately, the end goal of this Ransomware is to spread within a target network, exfiltrate data, and eventually encrypt important files. Once these actions have been carried out, they request payment from the victim’s to decrypt their files and to keep them from making the exfiltrated data public.
Due to there being unrelated affiliates carrying out LockBit attacks, the TTP’s observed can vary. However, we can look at some of the most common behaviors.
To learn more about LockBit IOC’s and deeper technical analysis, see these links below:
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-165a
https://laurentiu-raducu.medium.com/lockbit-3-0-ransomware-analysis-198b1d4b75a3
https://www.txone.com/blog/malware-analysis-lockbit-3-0/
TTP/Detection Strategies
We’ll be covering a few of the observed TTP’s and will map them to the MITRE ATT&CK framework. After each TTP, some basic detection strategies will be listed along with sample Sigma rules. Disclaimer: It is critical to understand your network environment when creating detection rules - make sure to test and tune any new rule in a non-production environment. All of the Sigma rules mentioned in this post are included as reference examples and should not be implemented in a production environment without prior testing.
Initial Access
External Remote Services - T1133 (Link for more info)
LockBit affiliates have been observed exploiting RDP (Remote Desktop Protocol) to gain access to victims’ networks.
Detection Strategy - T1133
Firstly, RDP should never be exposed to the Internet (unfortunately, this is still too common). However, you can monitor Windows event logs for this type of behavior.
See this Sigma rule as a good reference point:
title: External Remote RDP Logon from Public IP
id: 259a9cdf-c4dd-4fa2-b243-2269e5ab18a2
related:
- id: 78d5cab4-557e-454f-9fb9-a222bd0d5edc
type: derived
status: test
description: Detects successful logon from public IP address via RDP. This can indicate a publicly-exposed RDP port.
references:
- https://www.inversecos.com/2020/04/successful-4624-anonymous-logons-to.html
-author: Micah Babinski (@micahbabinski), Zach Mathis (@yamatosecurity)
date: 2023/01/19
modified: 2023/03/16
tags:
- attack.initial_access
- attack.credential_access
- attack.t1133
- attack.t1078
- attack.t1110
logsource:
product: windows
service: security
detection:
selection:
EventID: 4624
LogonType: 10
filter_ipv4:
IpAddress|cidr:
- '127.0.0.0/8'
- '10.0.0.0/8'
- '172.16.0.0/12'
- '192.168.0.0/16'
filter_ipv6:
- IpAddress: '::1' # IPv6 loopback
- IpAddress|startswith:
- 'fe80:' # link-local address
- 'fc' # private address range fc00::/7
- 'fd' # private address range fc00::/7
filter_empty:
IpAddress: '-'
condition: selection and not 1 of filter_*
falsepositives:
- Legitimate or intentional inbound connections from public IP addresses on the RDP port.
level: mediumPhishing - T1566 (Link for more info)
LockBit affiliates have been observed using phishing to gain access to victims' networks.
Image generated by DALL-E
Detection Strategy - T1566
Phishing is all too common for threat actors of all types to implement; simply because it works. For prevention, companies should have some sort of email protection/email security services in place along with the usual stuff (awareness training, multi-factor authentication, etc.). Regarding detection, there’s multiple avenues you can go down to alert on a possible successful phishing attempt. To get the thinking process started, take a look at this Sigma rule. Since one common phishing method is to send infected Microsoft Office (Word, Excel, etc.) attachments and tricking users into opening them, this rule is looking for Window’s Shells that have been spawned from a number of different Office applications. While I’m sure there are some exceptions, typical users should not be creating/running Microsoft Office files intentionally in this manner.
title: Microsoft Office Product Spawning Windows Shell
id: 438025f9-5856-4663-83f7-52f878a70a50
status: test
description: Detects a Windows command and scripting interpreter executable started from Microsoft Word, Excel, Powerpoint, Publisher and Visio
author: Michael Haag, Florian Roth, Markus Neis, Elastic, FPT.EagleEye Team
references:
- https://www.hybrid-analysis.com/sample/465aabe132ccb949e75b8ab9c5bda36d80cf2fd503d52b8bad54e295f28bbc21?environmentId=100
- https://mgreen27.github.io/posts/2018/04/02/DownloadCradle.html
date: 2018/04/06
modified: 2022/02/23
logsource:
category: process_creation
product: windows
detection:
selection:
ParentImage|endswith:
- '\WINWORD.EXE'
- '\EXCEL.EXE'
- '\POWERPNT.exe'
- '\MSPUB.exe'
- '\VISIO.exe'
- '\MSACCESS.EXE'
- '\EQNEDT32.EXE'
Image|endswith:
- '\cmd.exe'
- '\powershell.exe'
- '\wscript.exe'
- '\cscript.exe'
- '\sh.exe'
- '\bash.exe'
- '\scrcons.exe'
- '\schtasks.exe'
- '\regsvr32.exe'
- '\hh.exe'
- '\wmic.exe' # https://app.any.run/tasks/c903e9c8-0350-440c-8688-3881b556b8e0/
- '\mshta.exe'
- '\rundll32.exe'
- '\msiexec.exe'
- '\forfiles.exe'
- '\scriptrunner.exe'
- '\mftrace.exe'
- '\AppVLP.exe'
- '\svchost.exe' # https://www.vmray.com/analyses/2d2fa29185ad/report/overview.html
- '\msbuild.exe' # https://github.com/elastic/detection-rules/blob/main/rules/windows/defense_evasion_execution_msbuild_started_by_office_app.toml
condition: selection
fields:
- CommandLine
- ParentCommandLine
falsepositives:
- Unknown
level: high
tags:
- attack.execution
- attack.t1204.002Execution
System Services: Service Execution - T1569.002 (Link for more info)
Affiliates have been observed using LockBit 3.0 with PsExec to execute commands or payloads.
Detection Strategy - T1569.002
While PsExec is a legitimate administrative tool, it is also widely used by threat actors. If you’re in an environment where PsExec should never be used, it probably makes sense to detect on any observed activity.
See this Sigma rule as a good reference point:
title: PsExec Service File Creation
id: 259e5a6a-b8d2-4c38-86e2-26c5e651361d
related:
- id: 42c575ea-e41e-41f1-b248-8093c3e82a28
type: derived
status: test
description: Detects default PsExec service filename which indicates PsExec service installation and execution
references:
- https://www.jpcert.or.jp/english/pub/sr/ir_research.html
- https://jpcertcc.github.io/ToolAnalysisResultSheet
author: Thomas Patzke
date: 2017/06/12
modified: 2022/10/26
tags:
- attack.execution
- attack.t1569.002
- attack.s0029
logsource:
category: file_event
product: windows
detection:
selection:
TargetFilename|endswith: '\PSEXESVC.exe'
condition: selection
falsepositives:
- Unknown
level: lowCollection
Archive Collected Data: Archive via Utility - T1560.001 (Link for more info)
Affiliates have been observed using 7-zip to compress and/or encrypt collected data prior to exfiltration.
Detection Strategy - T1560.001
7-zip is another legitimate tool that is used in normal operations, but it is also often used by threat actors before they exfiltrate data. As many Ransomware groups are carrying out “Double Extortion” attacks, it is important to detect related behavior and stop the activity before any protected data has been stolen. See this example rule as a starting point. It’s also important to note that there are other compression tools out there, so it would be helpful to expand coverage of this detection rule.
title: Compress Data and Lock With Password for Exfiltration With 7-ZIP
id: 9fbf5927-5261-4284-a71d-f681029ea574
status: test
description: An adversary may compress or encrypt data that is collected prior to exfiltration using 3rd party utilities
references:
- https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1560.001/T1560.001.md
author: frack113
date: 2021/07/27
modified: 2023/03/13
tags:
- attack.collection
- attack.t1560.001
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Description|contains: '7-Zip'
- Image|endswith:
- '\7z.exe'
- '\7zr.exe'
- '\7za.exe'
- OriginalFileName:
- '7z.exe'
- '7za.exe'
selection_password:
CommandLine|contains: ' -p'
selection_action:
CommandLine|contains:
- ' a '
- ' u '
condition: all of selection_*
falsepositives:
- Legitimate activity is expected since compressing files with a password is common.
level: mediumImpact
Defacement: Internal Defacement - T1491.001 (Link for more info)
Like most Ransomware variants, LockBit 3.0 changes the host system’s wallpaper and icons to the LockBit 3.0 images.
Detection Strategy - T1491.001
By this point, hopefully other detections have fired and the system is isolated, but it still doesn’t hurt have a detection rule in place to catch this particular behavior. Keep in mind it is possible to get false positives if an Administrator is changing wallpapers in a similar manner. Make sure to tune this sample rule to the environment:
title: Potentially Suspicious Desktop Background Change Via Registry
id: 85b88e05-dadc-430b-8a9e-53ff1cd30aae
related:
- id: 8cbc9475-8d05-4e27-9c32-df960716c701
type: similar
status: experimental
description: |
Detects regsitry value settings that would replace the user's desktop background.
This is a common technique used by malware to change the desktop background to a ransom note or other image.
references:
- https://www.attackiq.com/2023/09/20/emulating-rhysida/
- https://research.checkpoint.com/2023/the-rhysida-ransomware-activity-analysis-and-ties-to-vice-society/
- https://www.trendmicro.com/en_us/research/23/h/an-overview-of-the-new-rhysida-ransomware.html
- https://www.virustotal.com/gui/file/a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6/behavior
- https://admx.help/?Category=Windows_10_2016&Policy=Microsoft.Policies.WindowsDesktop::Wallpaper
- https://admx.help/?Category=Windows_10_2016&Policy=Microsoft.Policies.ControlPanelDisplay::CPL_Personalization_NoDesktopBackgroundUI
author: Nasreddine Bencherchali (Nextron Systems), Stephen Lincoln @slincoln-aiq (AttackIQ)
date: 2023/12/21
tags:
- attack.defense_evasion
- attack.impact
- attack.t1112
- attack.t1491.001
logsource:
product: windows
category: registry_set
detection:
selection_keys:
TargetObject|contains:
- 'Control Panel\Desktop'
- 'CurrentVersion\Policies\ActiveDesktop'
- 'CurrentVersion\Policies\System'
selection_values_1:
TargetObject|endswith: 'NoChangingWallpaper'
Details: 'DWORD (0x00000001)' # Prevent changing desktop background
selection_values_2:
TargetObject|endswith: '\Wallpaper'
selection_values_3:
TargetObject|endswith: '\WallpaperStyle'
Details: '2' # Stretch
filter_main_svchost:
# Note: Excluding GPO changes
Image|endswith: '\svchost.exe'
condition: selection_keys and 1 of selection_values_* and not 1 of filter_main_*
falsepositives:
- Administrative scripts that change the desktop background to a company logo or other image.
level: mediumMalware Detection
Ensure that your Anti-Virus (or other endpoint tool of choice) has signature based detections in place to identity the LockBit payloads. You can also look into automated integrations with VirusTotal as well as getting started with Yara.
Closing
These were just a few of the common TTP’s that LockBit affiliates use. Hopefully some find this format useful and it sparks up more thoughts on detection engineering in general.
If you made it this far please feel free to leave some feedback. Are there any other topics mentioned in this post (Sigma/Yara/MITRE ATT&CK) that need more explanation?




Thank you for helping me to expand my vocab and also detailing applicable SIGMA rules. Honestly, I didn't know much about SIGMA’s format but will certainly study up. Cheers!