Ransomware Series #2 - CL0P
A brief profile on CL0P Ransomware
Welcome to the second entry in the Ransomware Group series! Just like last time, we’ll start with some quick background information on the threat group and include links to IOC’s/more detailed analysis. Then we’ll dive into some tactics, techniques, and procedures (TTP’s) mapped to the MITRE ATT&CK framework - along with basic detection strategies (this time a mix of Snort, Sigma, and YARA rules).
Reminder: It goes without saying that a holistic security program is needed and defense in depth strategies should be followed. I’ll be focusing more on detection strategies since these often get overlooked (plus they’re more interesting to me).
What is CL0P?
CL0P Profile from SOCRadar
CL0P is a Ransomware family/variant that operates in both a Ransomware-as-a-Service (RaaS) model and in targeted attacks carried out by certain threat groups such as TA505 and FIN11. Interestingly, the name comes from the word “Klop”, which translates to “Bed Bug” in Russian. CL0P was first observed in early 2019 and has become prolific ever since, resulting in many successful attacks and becoming one of the most dominant Ransomware variants over the last few years.
The CL0P group has remained relevant by shifting to double extortion schemes - many times they have forgone the file encryption process and have gone straight to the threat of making stolen data public. Additionally, they have shown sophistication in their attacks by finding and exploiting vulnerabilities to gain initial access instead of relying on Phishing emails or other security misconfigurations. In fact, some of the most high profile attacks have been the result of zero-day vulnerabilities: in Fortra GoAnywhere MFT and MOVEit Transfer/MOVEit Cloud. The latter of which thrusted the group into the spotlight as some of the victims were U.S. Government Agencies.
To learn more about CL0P IOC’s and deeper technical analysis, see these links below:
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-158a
https://www.securin.io/blog/all-about-clop-ransomware/
https://fourcore.io/blogs/clop-ransomware-history-adversary-simulation
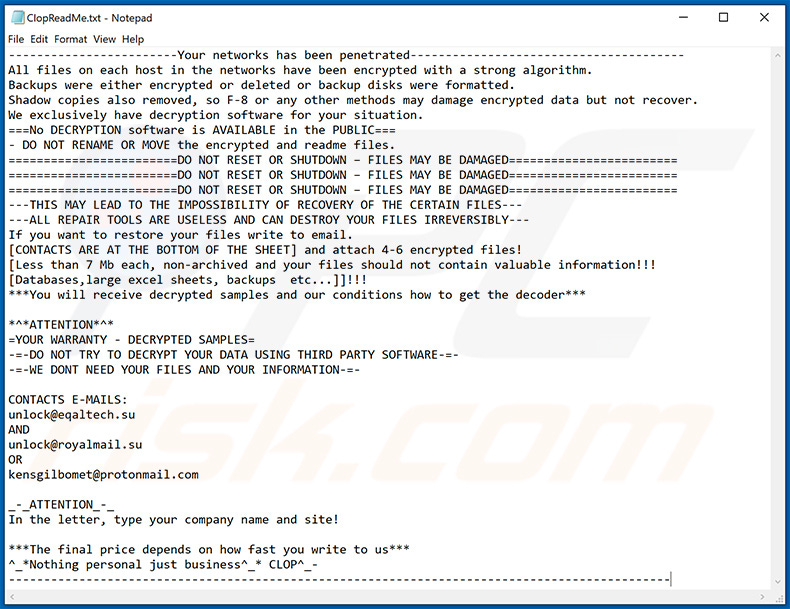
Example of “ClopReadMe.txt” ransom note from PCrisk
TTP/Detection Strategies
We’ll be covering a few of the observed TTP’s and will map them to the MITRE ATT&CK framework. After each TTP, some basic detection strategies will be listed along with sample rules (Snort/Sigma/YARA).
Disclaimer: It is critical to understand your network environment when creating detection rules - make sure to test and tune any new rule in a non-production environment. All of the rules mentioned in this post are included as reference examples and should not be implemented in a production environment without prior testing.
Initial Access
Exploit Public-Facing Application - T1190 (Link for more info)
The CL0P group has exploited numerous vulnerabilities, including the zero-day vulnerability affecting MOVEit Transfer software - CVE-2023-34362. This exploitation begins with a SQL Injection to infiltrate the MOVEit Transfer web application.
Detection Strategy - T1190
Some of the best strategies for detecting this type of technique (SQL Injection) are to use a WAF (Web Application Firewall) or Deep Packet Inspection (DPI) running through an IDS/IPS (Intrusion Detection System/Intrusion Prevention System). What is needed is any sort of tool that can inspect for common exploitation traffic and be on the lookout for SQL Injection type strings.
See these two example Snort rules as a good reference point:
#Rule to to detect possible sql injection using inline comments.
alert tcp any any -> any any (msg:”Possible SQL Injection — Inline Comments Detected”; flow:to_server,established; content:”GET”; nocase; http_method; content:”/”; http_uri; pcre:”/\?.*( — |#|\/\*)/”; sid:1000001;)
#Rule to detect boolean based sql injection
alert tcp any any -> any any (msg:”Possible Boolean-based Blind SQL Injection Attempt”; flow:to_server,established; content:”GET”; nocase; http_method; content:”/”; http_uri; pcre:”/\?.*(\bselect\b|\bunion\b|\band\b|\bor\b)(?:[^=]*=){2}[^&]*’/i”; sid:1000002;)For more information on how to write Snort rules, read through this link. For more information on SQL Injection, see this link.
Note: It’s important to have a vulnerability/patch management strategy in place to apply known exploited/critical patches ASAP.
Execution
Shared Modules - T1129 (Link for more info)
CL0P actors use Truebot to download additional modules.
Detection Strategy - T1129
Truebot malware has been frequently tied to CL0P activities, but it is also used by other threat actors and for different types of attacks. It’s a good idea to have detections in place for Truebot malware and to stop an attack early. See this Snort rule to help detect Truebot (found in this CISA report).
alert tcp any any -> any any (msg:”TRUEBOT: Client HTTP Header”; sid:x; rev:1; flow:established,to_server; content:”Mozilla/112.0 (compatible|3b 20 4d 53 49 45 20 31 31 2e 30 3b 20 57 69 6e 64 6f 77 73 20 4e 54 20 31 30 2e 30 30 29|”; http_header; nocase; classtype:http-header; metadata:service http;)In addition to the Snort rule, here is a YARA rule to detect Truebot downloader samples (found in the same CISA report).
rule CISA_10445155_01 : TRUEBOT downloader
{
meta:
Author = "CISA Code & Media Analysis"
Incident = "10445155"
Date = "2023-05-17"
Last_Modified = "20230523_1500"
Actor = "n/a"
Family = "TRUEBOT"
Capabilities = "n/a"
Malware_Type = "downloader"
Tool_Type = "n/a"
Description = "Detects TRUEBOT downloader samples"
SHA256 = "7d75244449fb5c25d8f196a43a6eb9e453652b2185392376e7d44c21bd8431e7" strings:
$s1 = { 64
$s2 = { 4e
$s3 = { 59
$s4 = { 72
$s5 = { 4c
$s6 = { 54
$s7 = { 54
condition:
5 of them
}Defense Evasion
Hijack Execution Flow: DLL Side-Loading - T1574.002 (Link for more info)
CL0P actors use Truebot to side load DLLs.
Detection Strategy - T1574.002
This same technique is used by many types of malware and threat actors. As such, detection rules to identify this type of behavior can prove to be very valuable. For more information on DLL Side-Loading, see this excellent write-up from Mandiant.
See this Sigma rule as a good reference point:
title: Potential DLL Sideloading Of Non-Existent DLLs From System Folders
id: 6b98b92b-4f00-4f62-b4fe-4d1920215771
related:
- id: df6ecb8b-7822-4f4b-b412-08f524b4576c # FileEvent rule
type: similar
- id: 602a1f13-c640-4d73-b053-be9a2fa58b77
type: obsoletes
status: test
description: |
Detects DLL sideloading of system DLLs that are not present on the system by default (at least not in system directories).
Usually this technique is used to achieve UAC bypass or privilege escalation.
references:
- https://decoded.avast.io/martinchlumecky/png-steganography/
- https://posts.specterops.io/lateral-movement-scm-and-dll-hijacking-primer-d2f61e8ab992
- https://clement.notin.org/blog/2020/09/12/CVE-2020-7315-McAfee-Agent-DLL-injection/
- https://github.com/Wh04m1001/SysmonEoP
- https://www.hexacorn.com/blog/2013/12/08/beyond-good-ol-run-key-part-5/
- http://remoteawesomethoughts.blogspot.com/2019/05/windows-10-task-schedulerservice.html
author: Nasreddine Bencherchali (Nextron Systems), SBousseaden
date: 2022/12/09
modified: 2024/01/10
tags:
- attack.defense_evasion
- attack.persistence
- attack.privilege_escalation
- attack.t1574.001
- attack.t1574.002
logsource:
category: image_load
product: windows
detection:
selection:
ImageLoaded|endswith:
# Add other DLLs
- ':\Windows\System32\TSMSISrv.dll'
- ':\Windows\System32\TSVIPSrv.dll'
- ':\Windows\System32\wbem\wbemcomn.dll'
- ':\Windows\System32\WLBSCTRL.dll'
- ':\Windows\System32\wow64log.dll'
- ':\Windows\System32\WptsExtensions.dll'
filter_main_ms_signed:
Signed: 'true'
SignatureStatus: 'Valid'
# There could be other signatures (please add when found)
Signature: 'Microsoft Windows'
condition: selection and not 1 of filter_main_*
falsepositives:
- Unknown
level: highDiscovery
Remote System Discovery - T1018 (Link for more info)
CL0P actors use Cobalt Strike to expand network access after gaining access to the Active Directory (AD) servers.
Detection Strategy - T1018
Cobalt Strike is one of the most popular adversary emulation and red team operations platforms available on the market. Not only is it widely used by Penetration Testers, but many threat actors have taken it and use it for malicious purposes. It is highly, highly recommended to have detections in place to catch Cobalt Strike activity. Luckily for us, the good folks at the Google Cloud Threat Intelligence Team saw the value of providing multiple YARA rules for defenders to detect potentially malicious Cobalt Strike activity. All of the rules are useful, so I suggest taking a look here.
Exfiltration
Exfiltration Over C2 Channel - T1041 (Link for more info)
CL0P actors exfiltrate data over C2 channels.
Detection Strategy - T1041
Exfiltration is one of the last steps in a CL0P attack. By this time, hopefully other detections have fired and the attack has been stopped. Even still, it’s critical that any attempts at data exfiltration be caught - once the data leaves the network, there’s no getting it back and all control of it is lost. With that said, there are many different methods used to carry out this behavior and in turn many different detection strategies possible. I have included an example rule below to help get the thought process started. Note: This example rule is specific to use of the rclone utility - more coverage would be needed for other exfiltration methods.
title: PUA - Rclone Execution
id: e37db05d-d1f9-49c8-b464-cee1a4b11638
related:
- id: a0d63692-a531-4912-ad39-4393325b2a9c
type: obsoletes
- id: cb7286ba-f207-44ab-b9e6-760d82b84253
type: obsoletes
status: test
description: Detects execution of RClone utility for exfiltration as used by various ransomwares strains like REvil, Conti, FiveHands, etc
references:
- https://research.nccgroup.com/2021/05/27/detecting-rclone-an-effective-tool-for-exfiltration/
- https://thedfirreport.com/2021/03/29/sodinokibi-aka-revil-ransomware
- https://us-cert.cisa.gov/ncas/analysis-reports/ar21-126a
- https://labs.sentinelone.com/egregor-raas-continues-the-chaos-with-cobalt-strike-and-rclone
- https://www.splunk.com/en_us/blog/security/darkside-ransomware-splunk-threat-update-and-detections.html
author: Bhabesh Raj, Sittikorn S, Aaron Greetham (@beardofbinary) - NCC Group
date: 2021/05/10
modified: 2023/03/05
tags:
- attack.exfiltration
- attack.t1567.002
logsource:
product: windows
category: process_creation
detection:
selection_specific_options:
CommandLine|contains|all:
- '--config '
- '--no-check-certificate '
- ' copy '
selection_rclone_img:
- Image|endswith: '\rclone.exe'
- Description: 'Rsync for cloud storage'
selection_rclone_cli:
CommandLine|contains:
- 'pass'
- 'user'
- 'copy'
- 'sync'
- 'config'
- 'lsd'
- 'remote'
- 'ls'
- 'mega'
- 'pcloud'
- 'ftp'
- 'ignore-existing'
- 'auto-confirm'
- 'transfers'
- 'multi-thread-streams'
- 'no-check-certificate '
condition: selection_specific_options or all of selection_rclone_*
fields:
- CommandLine
- ParentCommandLine
- Details
falsepositives:
- Unknown
level: highMalware Detection
Ensure that your Anti-Virus (or other endpoint tool of choice) has signature based detections in place to identity the CL0P related payloads.
Closing
These were just a few of the common TTP’s that the CL0P group and affiliates use. As we have seen, having detections all along the MITRE ATT&CK framework help to catch attacks at every stage, increasing the likelihood that at least 1 stage of an attack can be detected.
If you made it this far please feel free to leave some feedback!



Excellent overview. This pesky bunch has been quite busy and a regular feature on the national news these days. “Nothing personal just business” How rude. Thanks for the knowledge once again!