Word Default Template Persistence - Part 1
T1137.001 - Establishing persistence through the abuse of the Normal.dotm default Word template
Background
I’ve been highly interested in Detection Engineering concepts recently and have been using Atomic Red Team to test detection rules along the MITRE ATT&CK Framework. For those who don’t know, Atomic Red Team is an open-source tool that anyone can use to test their controls and detection capabilities. The library of tests are mapped to the ATT&CK techniques and are contributed to by the community. After a while, I became interested in seeing how I could contribute to the project. I started looking through the existing tests and finding techniques that were missing. That’s where T1137.001 - “Office Application Startup: Office Template Macros” got my attention.
Before I went into IT/Cybersecurity, I spent time in various Reporting Analyst roles (first at a Call Center, second at a for-profit University) creating/maintaining reports with super specialized tools like Excel and Word 😉 During this time, I became familiar with Macros and started trying to create simple ones to automate tedious actions and help make my life easier. Naturally, the idea of adding a Macro to a default Office template to establish persistence sounded like an ingenious idea that I wanted to try out. I decided to use Word for this project since the MuddyWater group has been observed exploiting it in a similar manner.
This will be a 3 part series:
Part 1 will focus on the overall concept and walk through the basic scenario manually.
Part 2 will cover the automation process via PowerShell.
Part 3 will cover the process to get the test properly formatted and submitted as a Pull Request to the Atomic Red Team Master branch.
Setting the Stage
All versions of Microsoft Word come with a default template, which is actually required for Word to operate. If the template were to become corrupted or missing, a new template would be automatically created. Users are able to save their own version of the default template so that every time they start a new or “Blank document”, it opens with whatever options they set (think things like default font, size, formatting, etc.).
The default template is named “Normal.dotm” and is stored here:
“C:\Users\<username>\AppData\Roaming\Microsoft\Templates\”
The main idea in this concept is to - add/inject a Macro to the Normal.dotm template, thereby allowing the malicious Macro to always be present, and then make it so that it auto-executes every time Word is opened. We eventually want the entire process scripted, but let’s walk through the process manually to see how it works.
Key Insights:
The “m” in the file extension “.dotm” means it’s a Macro enabled file.
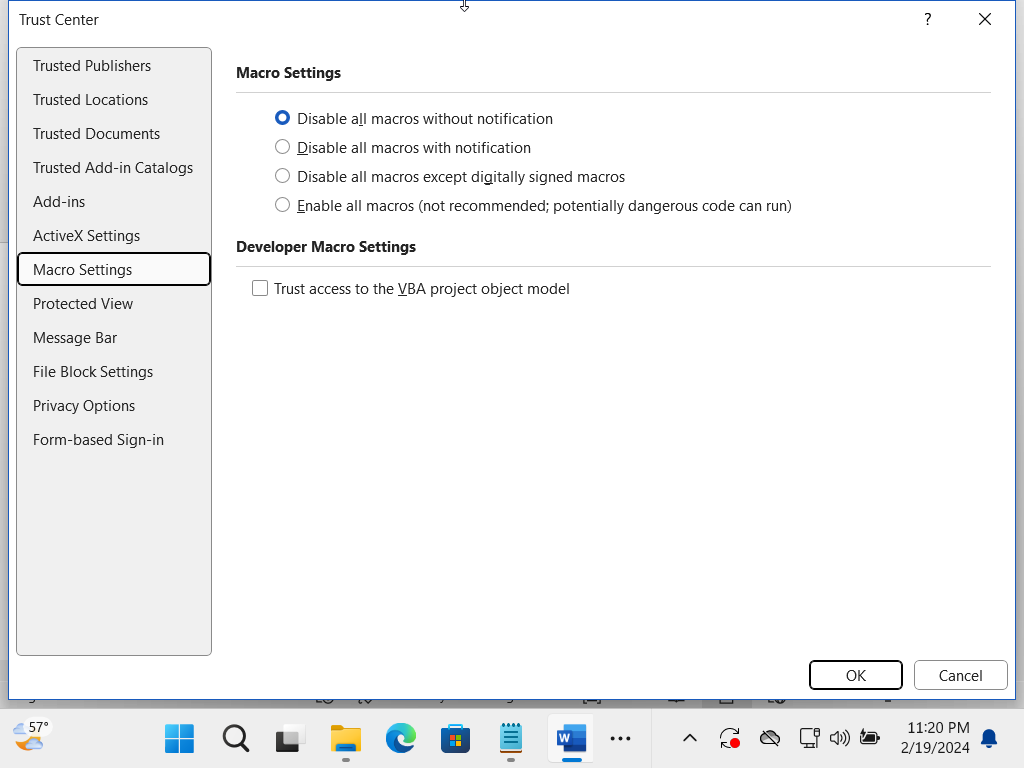
Since the Normal.dotm template is in a Trusted Location, the Macro can be executed even if “Disable all macros without notification” is set.
If ran manually within Word, even the “Trust access to the VBA project object model” can be left unchecked and it will still execute.
These are my Macro Settings used for this demo:
Creating a Macro
Quick Note: If you’re going to follow along, I recommend using a Virtual Machine or a Windows computer that you are ok to test things on (i.e. do not try this on a work computer). For these demos, I’m using a Windows 11 VM with Defender turned off.
The first thing we want to do is open the Normal.dotm template in Word. Launch Word, select Open, select the template in the file path:
“C:\Users\<username>\AppData\Roaming\Microsoft\Templates\”
Next we want to create a Macro. The easiest way to create a Macro is through the “Developer” tab, this tab is not visible by default.
You have to go to File>Options>Customize Ribbon, and then check the “Developer” box.
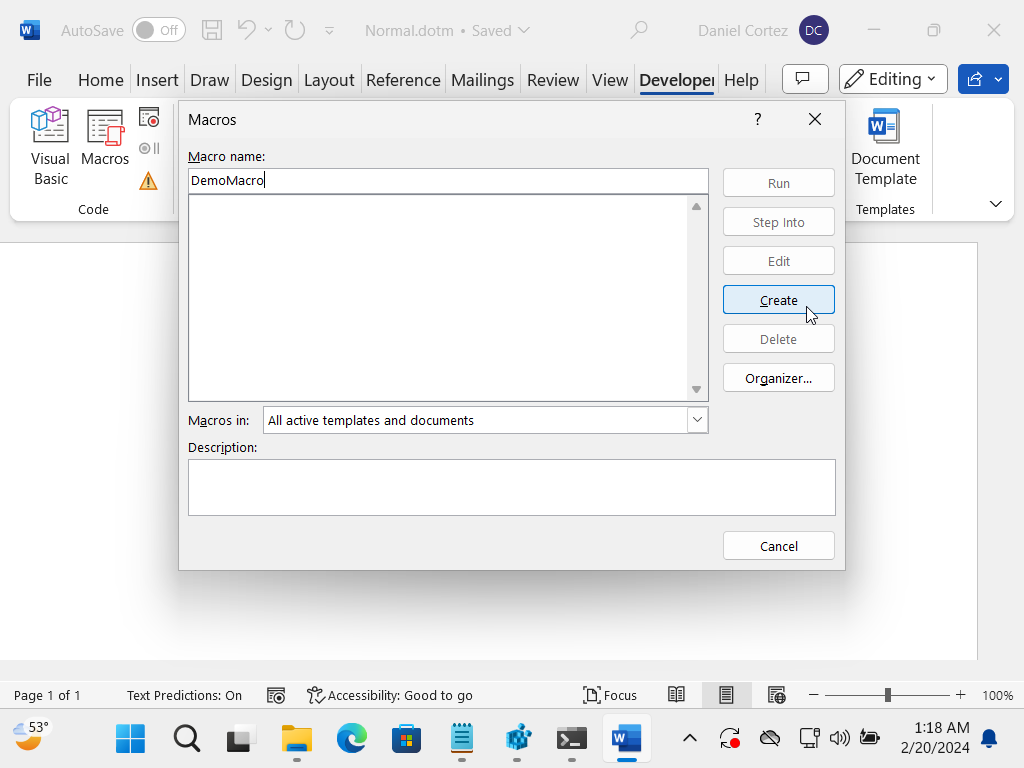
Once it gets added to the ribbon, click the “Developer” tab, click on “Macros” and enter a name for the Macro you want to create. I named this one “DemoMacro”.
In the VBA code for this first demo, we’re just going to have it open the legacy Windows Media Player application (dvdplay.exe)
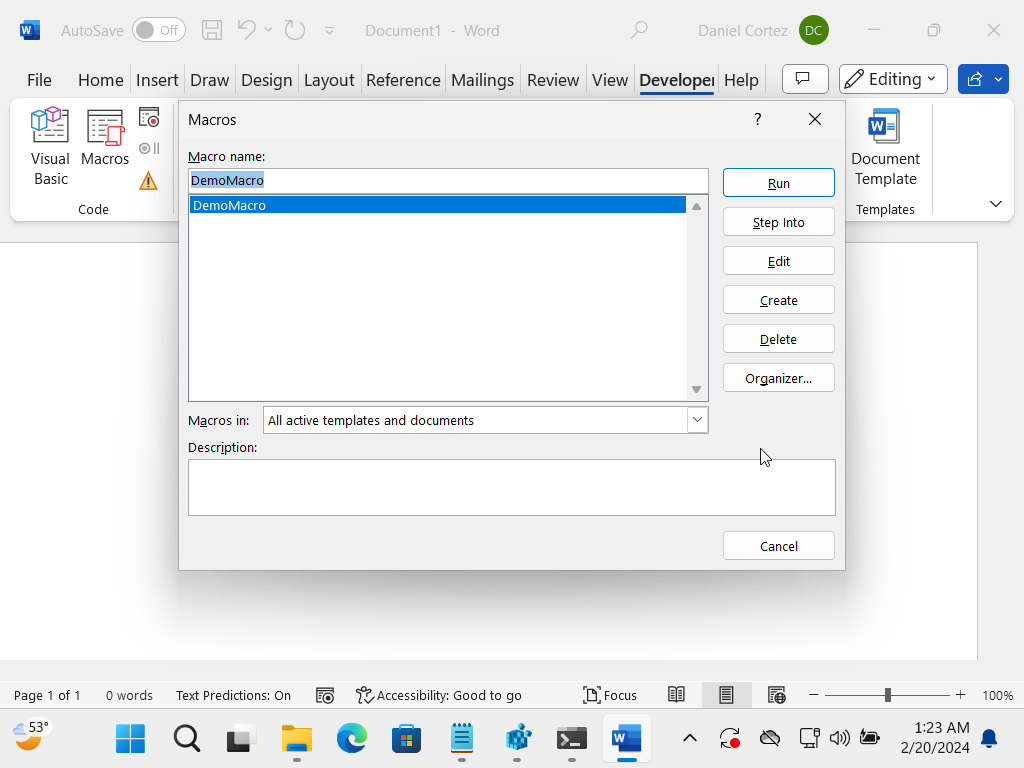
Once the code is entered, we want to click the save button, hit run (green play button), then select run again in the Macros pop-up.
If it ran successfully, the application window should open.
Now if we were to close out of everything and reopen Word, we can see that our DemoMacro still exists in “All active templates and documents”.
Auto-Execute
At this point, we know how to create a Macro in the default template. However, you may notice that we have to manually Run it - in order to have it execute. We want this to be as hands-off as possible. Therefore, the next thing we need to do is make it auto-execute every time Word launches.
It turns out that all we need to do to make this happen is: rename the Macro “AutoExec” - yes, it’s that simple.
So we need to edit the Macro, change the name, and click save.
Now we’re ready to close Word and re-launch it to see if it works. If it works as expected, the Windows Media Player application should launch every subsequent time that Word launches without any other interaction from us.
So now the Macro will execute any time this User were to launch Word: whether that’s via opening an existing document, starting a new document, or even just launching the application itself.
Conclusion
We really can have the Macro do anything we want. As you can imagine, a malicious actor can leverage this technique in many different ways.
What about something like: download a malicious executable and auto-execute it. Or: auto re-establish communication with a C2 channel. Or do a double-persistence mechanism like: keep creating a scheduled task to execute a program at a given time (if someone were to delete the scheduled task it would keep getting re-created every time Word launches, hence double-persistence).
Stay tuned for Part 2 where I break down how I chose to script out this test via PowerShell.