Previously, I wrote a blog post on “A Brief Overview of Sigma” - which has some overlap and relationship with Sysmon. It made sense to continue this series and give more insight into this other popular tool.
A Brief Overview of Sigma
If you've read any of my posts, you've noticed that I'm a big proponent of the Sigma project. Whenever I set out to write detection rules, I do so in this format.
This particular post is for readers who aren't yet familiar with Sysmon or who would like to learn more about it.
What is it?
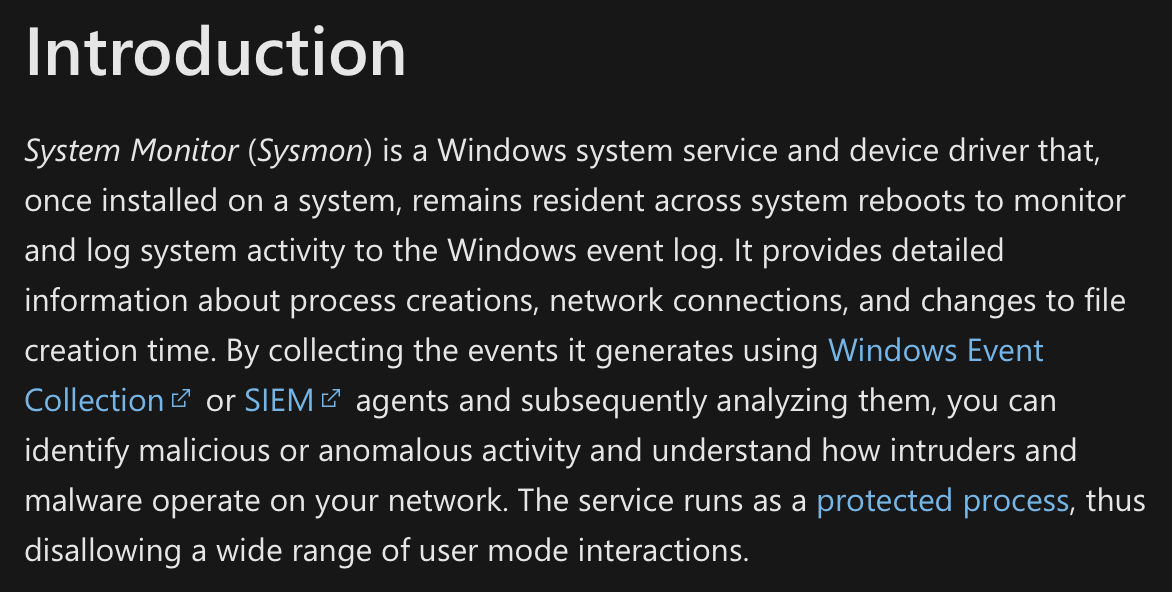
Sysmon, or System Monitor, was first released in 2014 as part of the SysInternals Suite of Microsoft utilities, largely created by Mark Russinovich. If you aren’t already familiar with SysInternals, I highly encourage looking through the available utilities (all free!). Many of them are in use everyday in Incident Response, Forensics, and other Security Operations (PSExec, ProcessMonitor, Autoruns, and TCPView are just a few of my favorites).
Note: If you’d like to hear the history of SysInternals from Mark himself, I found this video incredibly interesting:
Back to Sysmon -
Essentially, Sysmon allows for greater visibility into Windows endpoints by expanding on what gets captured in default Windows Event Logs. It’s important to note that Sysmon is not included by default with the Windows Operating System (OS) and requires a separate install, along with a Configuration File. See the official description below:
What problem does it solve?
More Telemetry
If you’ve seen Windows Event Logs, you know that they can be lacking in information - and unless you memorized all of the most useful Event ID’s, you probably need to refer to a Cheat Sheet in order to make sense of the logs.
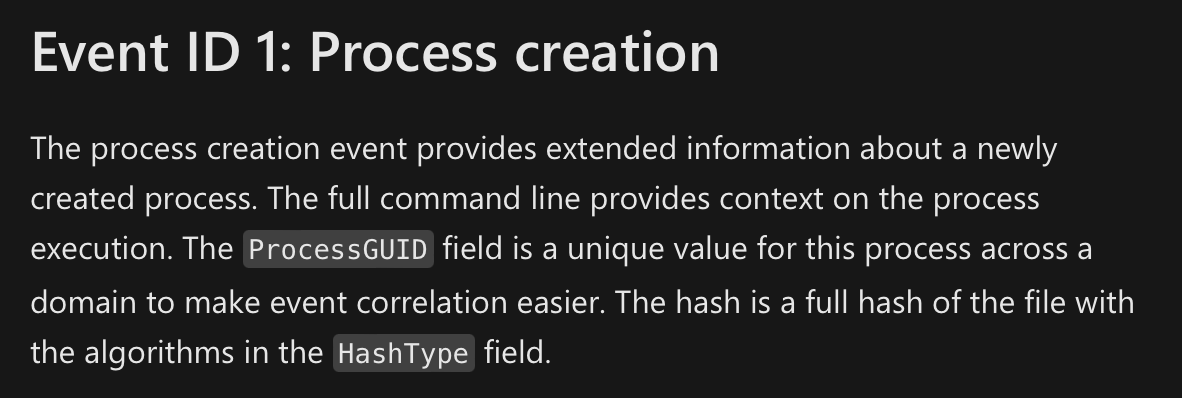
With Sysmon, you can get incredibly valuable information - such as Process Creation events with full command line for both current and parent processes! (See Sysmon Event ID 1: - Process Creation)
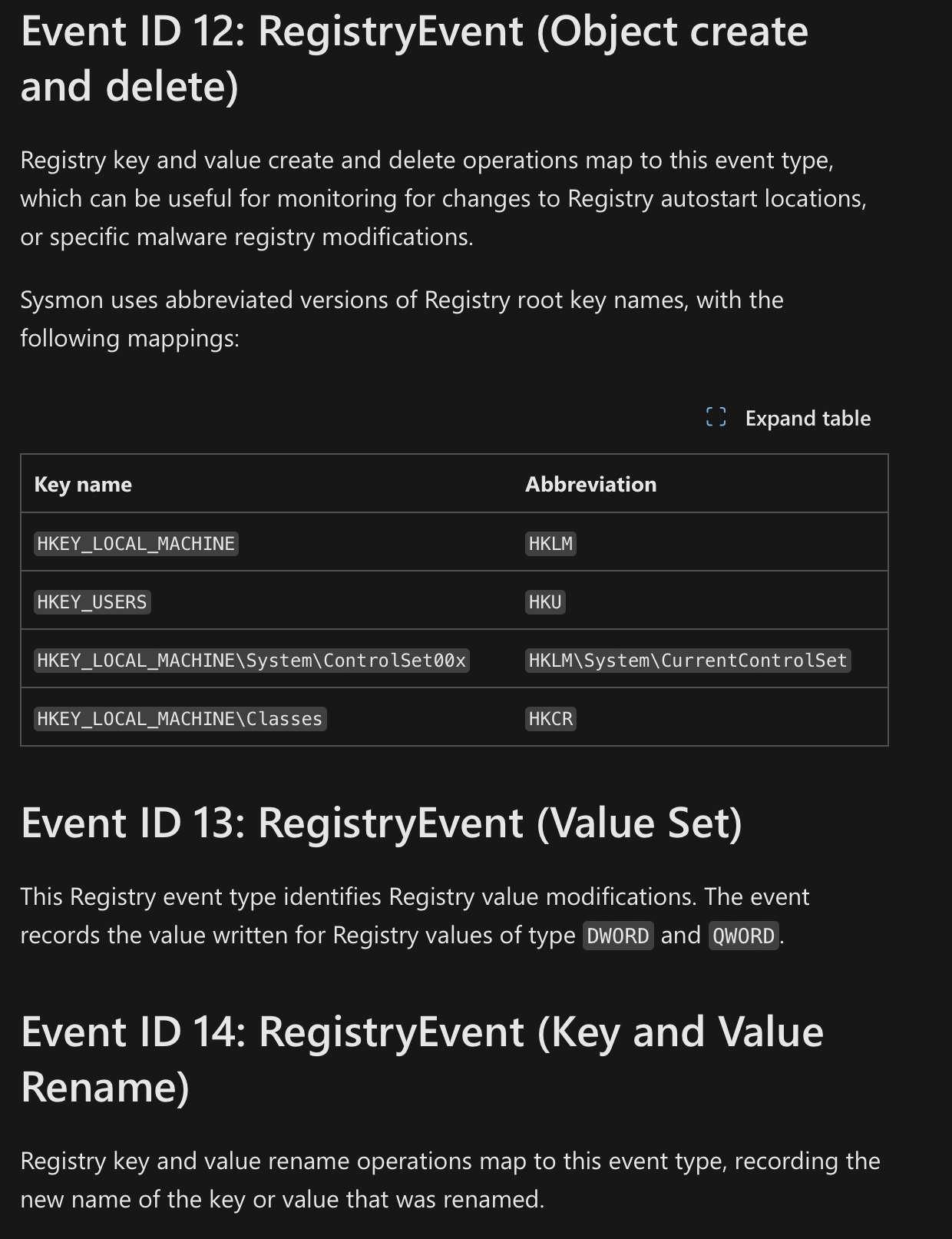
You can even get more details about Registry Modifications. (See Sysmon Event ID’s 12-14)
As you can see, you are able to gain massive insight into Windows endpoints just by installing this free tool!
Configurable
One major advantage of using Sysmon is that it is fully configurable. You can either borrow an existing configuration from someone, or create a fully custom config from scratch. Within the config file, you can specify things like which Registry keys you want to monitor, or which images (or executables) you want to exclude (say you have an EDR that you need to exclude from triggering events).
I recommend looking at these 2 options for existing configuration files:
https://github.com/olafhartong/sysmon-modular
https://github.com/Neo23x0/sysmon-config
Heads up: You may still see mentions of the SwiftOnSecurity config, while it was a good starting point, it hasn’t been updated in over 3 years and is lacking references to the newest Sysmon Event ID’s 26-29.
Prevalent
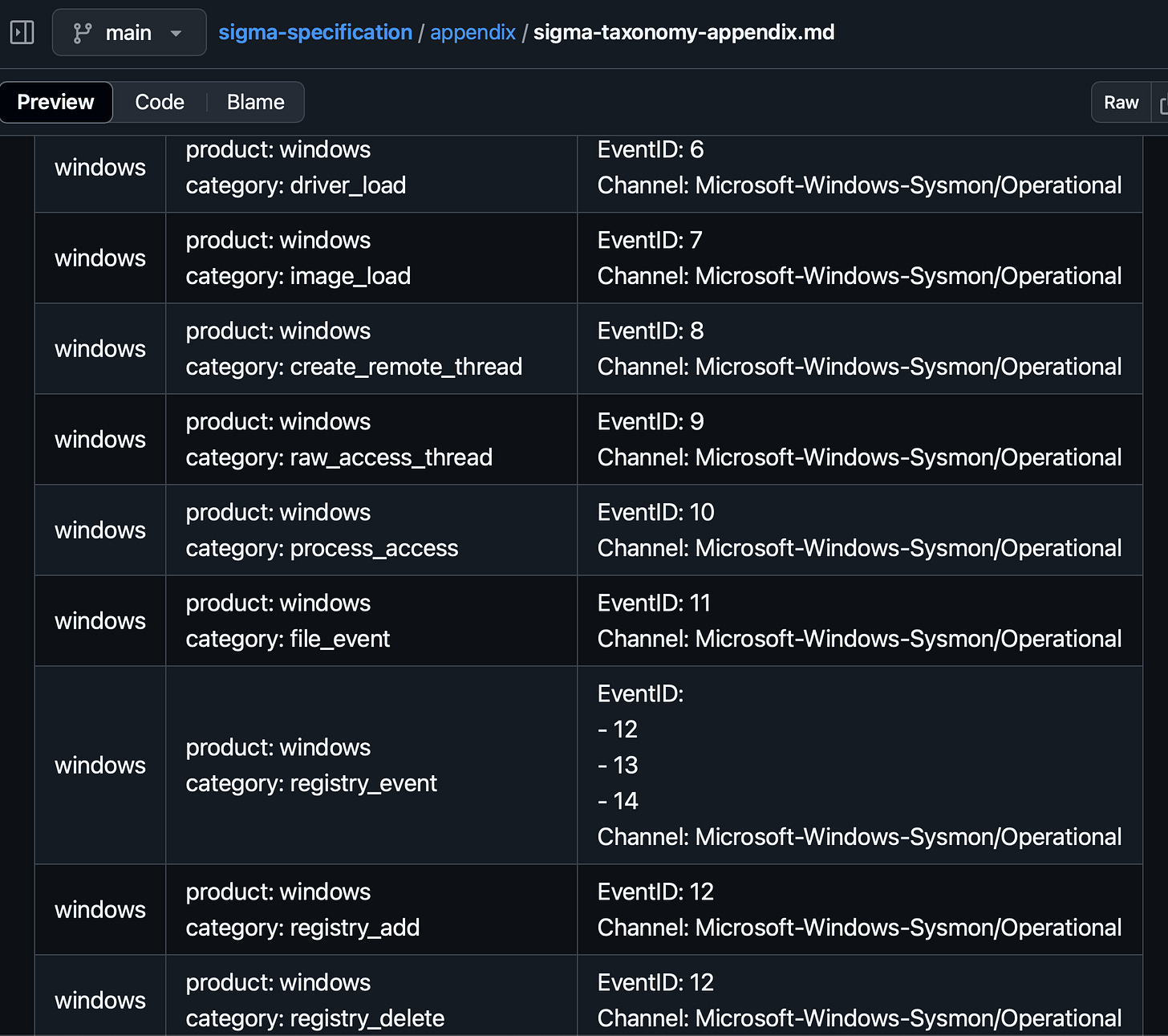
Another advantage of using Sysmon is that it is already widely in use. In fact, many EDR or SIEM tools rely on Sysmon events to complement their visibility and even build detections around them. It’s easy to see this in action if you look at Sigma rules and their Taxonomy. Look at all of the Sysmon events that Sigma Categories are pointing to: here
For example: This means that all of the ‘registry_event’ rules were written to target Sysmon EventID’s 12-14.
What does the process look like?
Not only is Sysmon free, but it is super simple to install and start using.
All you need to do is download the latest installer: should always be found here
You then need to download a configuration file, I prefer sysmon-modular as a starting point: here
Once you have both the installer and the configuration file, all you have to do is run the install command like below (the file paths will be different depending on where you placed the files):
sysmon -accepteula -i c:\windows\sysmonconfig.xmlOnce installed, you will start getting events within a few minutes. Events can be viewed within Event Viewer here:
Applications and Services Logs/Microsoft/Windows/Sysmon/Operational
You can also begin forwarding them to your Security tool of choice.
Bonus Video: Mark talking about the release of Sysmon
Conclusion
If you’ve read this, hopefully it was helpful and you now have more knowledge about Sysmon. If you haven’t already, I recommend giving it a try!