The topic of RMMs have been popping up on my radar pretty frequently over the past few months. With the recent launch of the LOLRMM project, it seemed like the perfect time to put together a quick blog post about it.
What are they?

RMM stands for Remote Monitoring and Management tools, which is mostly tracked within MITRE ATT&CK as “T1219: Remote Access Software”. RMMs are essentially tools that allow for remote administration of systems; whether that means taking full-control of a system to help out an end-user with an issue, pushing out software patches/updates/scripts, or providing system visibility of logged in users/running processes, etc.
Ultimately, these types of tools are legitimate technical support software and are widely used in all types of IT environments. Most notably, companies that outsource their IT Support through a Managed Service Provider (MSP) will typically have a RMM tool in their environment.
Why should defenders know about RMMs?
Since RMMs offer tons of administrative features and remote access, they are often used by malicious actors. From the MITRE ATT&CK entry:
Remote access software may be installed and used post-compromise as an alternate communications channel for redundant access or as a way to establish an interactive remote desktop session with the target system. They may also be used as a component of malware to establish a reverse connection or back-connect to a service or adversary-controlled system.
Additionally, since these are legitimate software, most security tools will not block or alert on their usage by default. This means that a malicious actor can use RMMs in compromised environments to maintain control of endpoints without being detected.
In fact, RMM usage by malicious actors is steadily increasing:
A report from Crowdstrike found a 70% year-over-year increase of RMM abuse. They also noted that ConnectWise ScreenConnect was the most abused tool between June 2023 and June 2024.
A report from the security firm ReliaQuest states that between 2022 and 2024, more than one third of the intrusions they responded to involved RMM tools.
In January of 2023, CISA released a Cybersecurity Advisory warning that cyber criminal actors were sending phishing emails to trick users into installing RMM software.
It’s also important to note that RMM abuse is a common TTP (Tactics, Techniques, and Procedures) of many prolific criminal groups like “Scattered Spider”, as well as Ransomware groups such as “ALHPV”, “Black Basta”, and “Conti”.
Detection Strategies
Luckily for us, the security community has collectively released useful information for defenders to increase their awareness of, and detect potential misuse of these tools.
Note: This is where understanding your network and knowing what is “normal” is critical. For example, if you know that the RMM tool AnyDesk is not used by anyone in your environment, then you should probably be alerted if it gets used - even if it was by a well-intentioned/legitimate user.
Which RMM tools to start with?
Looking at the total count of tools that are tracked within the LOLRMM project, there are over 260+(!) - many of which I’ve never seen used before. A good strategy here will be to look at tools that have actually been abused in real-world incidents. Here is a great list of RMM tools that have been used by Ransomware groups in actual attacks:
https://github.com/BushidoUK/Ransomware-Tool-Matrix/blob/main/Tools/RMM-Tools.md
We’ll be covering 2 of the tools on that list, while looking at some basic detection strategies and exploring their LOLRMM project entries. Note: we’ll be sticking to Windows examples, since this is the most prevalent use case.
Disclaimer: It is important to understand your environment when creating/running detection rules - make sure to test and tune any new rule in a non-production environment.
AnyDesk
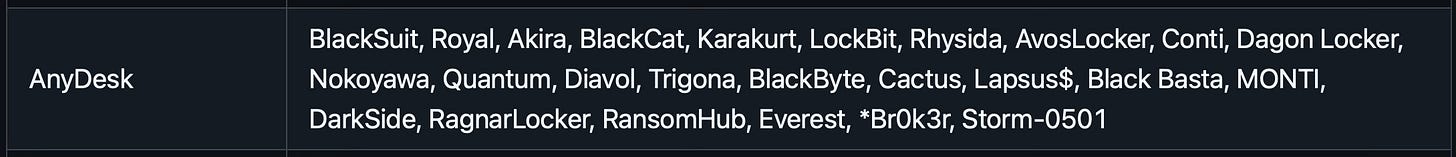
AnyDesk has been used by numerous different Ransomware groups, including BlackSuit, Royal, and LockBit:
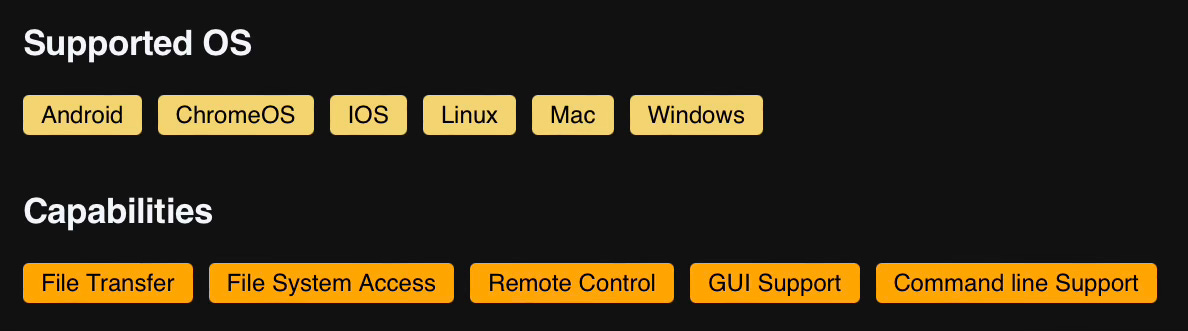
Within LOLRMM, we can see things like the supported operating systems and capabilities of the specific tool:
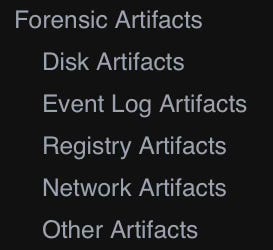
Most importantly, the LOLRMM entry contains different Forensic Artifacts that are tied to each tool:
We can take these different types of Artifacts and craft detection rules around them, allowing us to be alerted if AnyDesk usage is happening in our environment. One of the best places to be monitoring for installation/usage is the Registry. The LOLRMM entry contains numerous examples of where the AnyDesk tool creates Artifacts in the Registry:
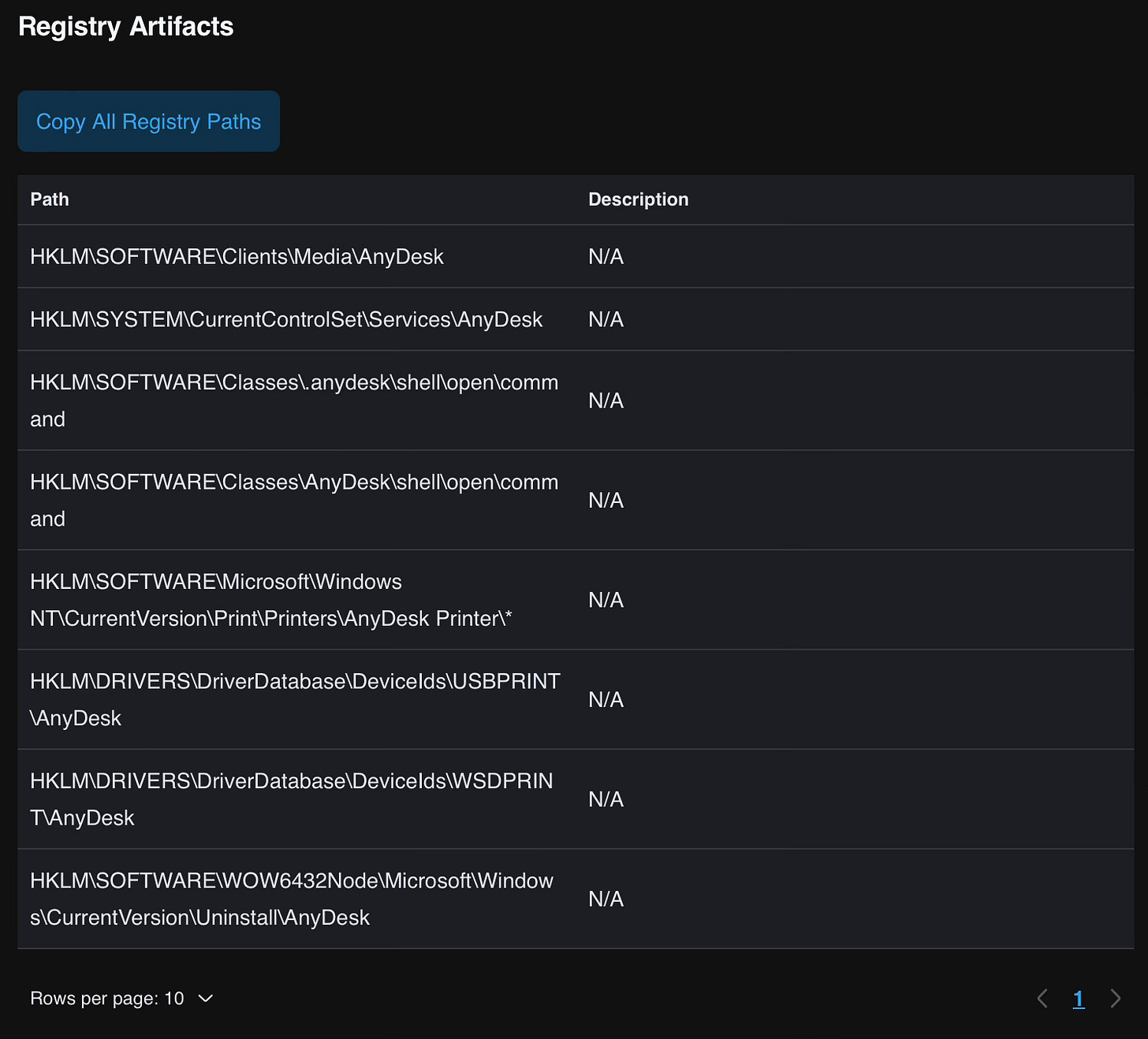
With this information, we can craft a detection rule that will trigger an alert if any of these Registry Artifacts are created (the LOLRMM maintainers have already authored this exact rule):
title: Potential AnyDesk RMM Tool Registry Activity
logsource:
product: windows
category: registry_event
detection:
selection:
TargetObject|contains:
- HKLM\SOFTWARE\Clients\Media\AnyDesk
- HKLM\SYSTEM\CurrentControlSet\Services\AnyDesk
- HKLM\SOFTWARE\Classes\.anydesk\shell\open\command
- HKLM\SOFTWARE\Classes\AnyDesk\shell\open\command
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Print\Printers\AnyDesk Printer\*
- HKLM\DRIVERS\DriverDatabase\DeviceIds\USBPRINT\AnyDesk
- HKLM\DRIVERS\DriverDatabase\DeviceIds\WSDPRINT\AnyDesk
- HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk
condition: selection
id: cd914a84-51f3-4342-be98-4e5bc1b7a55e
status: experimental
description: Detects potential registry activity of AnyDesk RMM tool
author: LOLRMM Project
date: 2024/08/07
tags:
- attack.execution
- attack.t1219
falsepositives:
- Legitimate use of AnyDesk
level: mediumNote: this is a Sigma rule, see this previous post for more information about Sigma
Another thing to monitor for tool usage is Network Connections. The LOLRMM entry contains a few examples of where the AnyDesk tool establishes Network Connections:
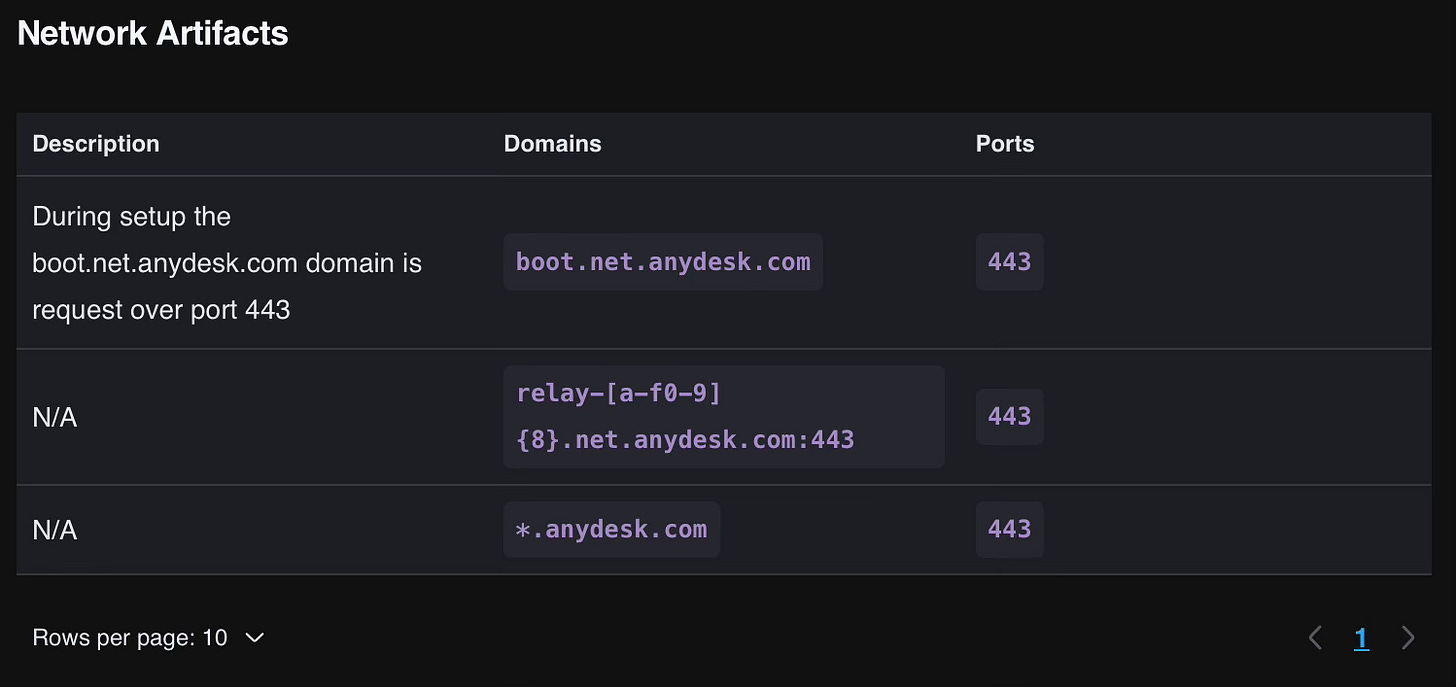
With this information, we can craft a detection rule that will trigger an alert if any of these Network Artifacts are detected (the LOLRMM maintainers have also authored this exact rule):
title: Potential AnyDesk RMM Tool Network Activity
logsource:
product: windows
category: network_connection
detection:
selection:
DestinationHostname|endswith:
- boot.net.anydesk.com
- relay-[a-f0-9]{8}.net.anydesk.com:443
- '*.anydesk.com'
condition: selection
id: bf3b1c02-8383-40df-8f5b-14e4a1e4fafe
status: experimental
description: Detects potential network activity of AnyDesk RMM tool
author: LOLRMM Project
date: 2024/08/07
tags:
- attack.execution
- attack.t1219
falsepositives:
- Legitimate use of AnyDesk
level: mediumScreenConnect
ScreenConnect has also been used by numerous different Ransomware groups:
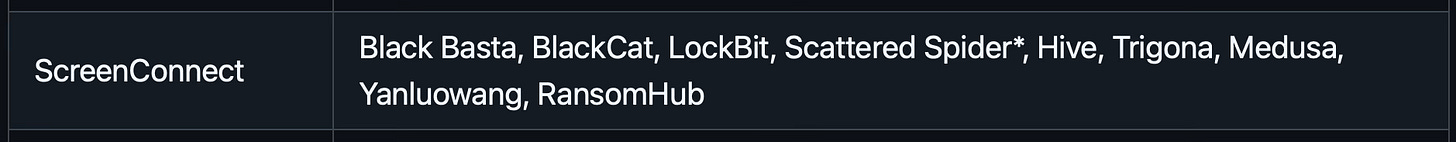
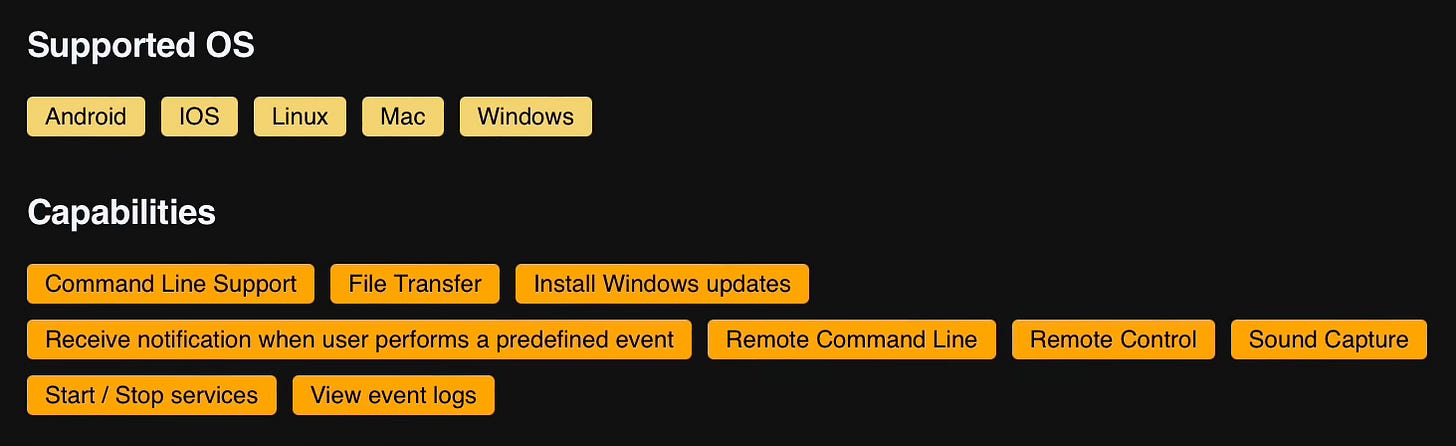
We can also see that it has many of the same capabilities as AnyDesk:
This time we’ll take a look at the different Disk Artifacts that get created when the tool gets installed/executed:
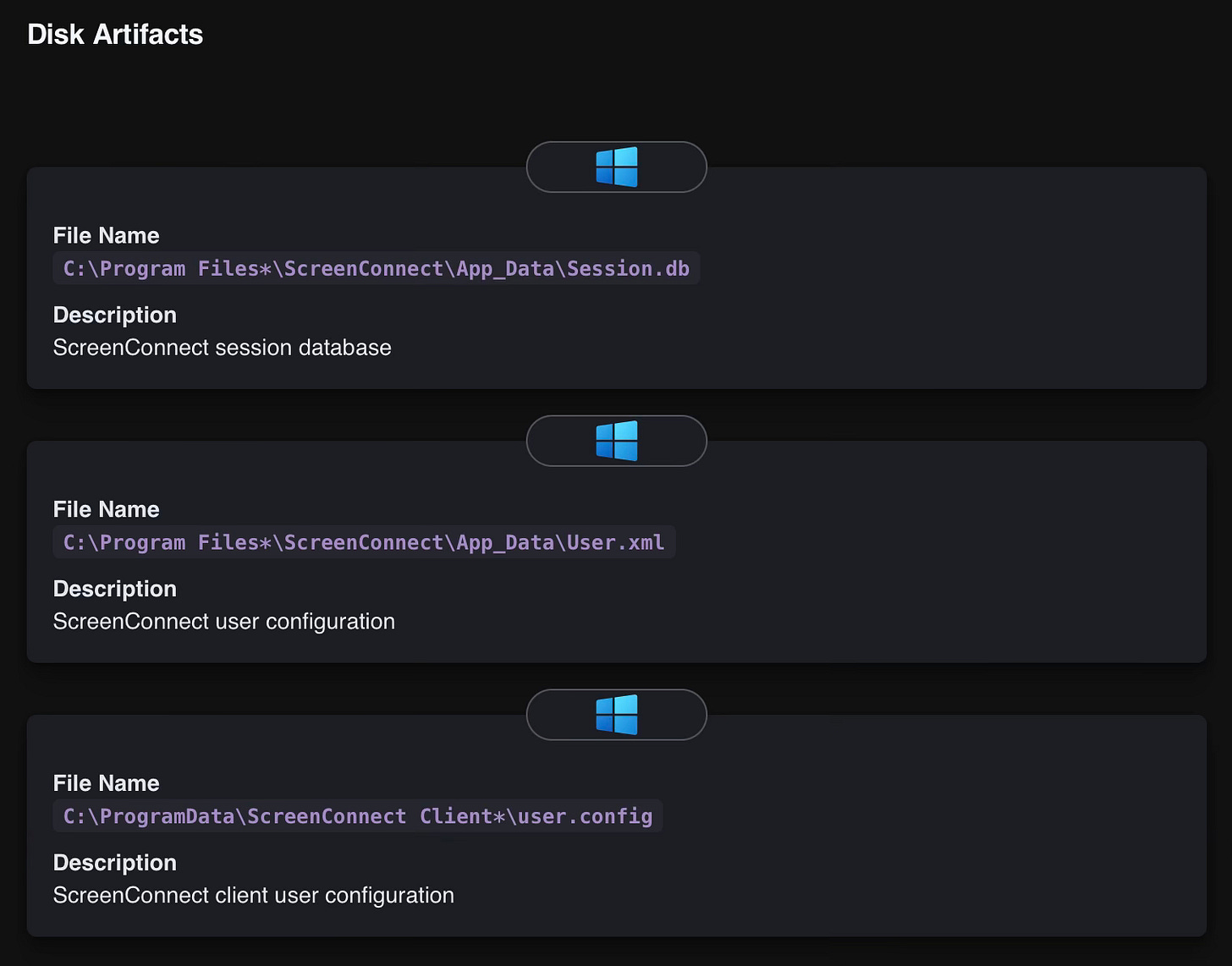
We can take these Disk Artifacts and craft a corresponding detection rule (the LOLRMM maintainers have also authored this exact rule):
title: Potential ScreenConnect RMM Tool File Activity
logsource:
product: windows
category: file_event
detection:
selection:
TargetFilename|endswith:
- C:\Program Files*\ScreenConnect\App_Data\Session.db
- C:\Program Files*\ScreenConnect\App_Data\User.xml
- C:\ProgramData\ScreenConnect Client*\user.config
condition: selection
id: adb2440e-8700-4ab3-9a1a-6b761826955f
status: experimental
description: Detects potential files activity of ScreenConnect RMM tool
author: LOLRMM Project
date: 2024/08/07
tags:
- attack.execution
- attack.t1219
falsepositives:
- Legitimate use of ScreenConnect
level: mediumClosing
While these types of tools are amazing enablers for remote IT departments, the capabilities and privilege level they bring can make them prime targets for threat actors. At the same time, it’s important to take a risk-based approach when it comes to crafting detection rules. Start with real-world examples of exploitation and prioritize from there.
Special thanks to the MagicSword crew for sharing the LOLRMM project with the community!



